As the time of writing, synced passkeys are still in public preview (December 2025).
Introduction
I recently switched to a new iPhone and was REALLY annoyed, that my Authenticator App backup went south… Time to try synced passkeys. I use Bitwarden as my password manager but any other should be good also if it’s supporting passkeys 😊
Prerequisites
Since I only have a Microsoft 365 Business Standard subscription on my private tenant, Entra ID Basic is sufficient (at least for now in the public preview). The free version of Bitwarden should also be enough even though I have a premium subscription, so take that with a grain of salt 😉
To get this to work, you need to install the browser add-in for Bitwarden.
Setup synced passkeys
We find the settings in the Authentication methods in Entra ID (Authentication methods – Microsoft Entra admin center)
We need to go to the FIDO2 settings
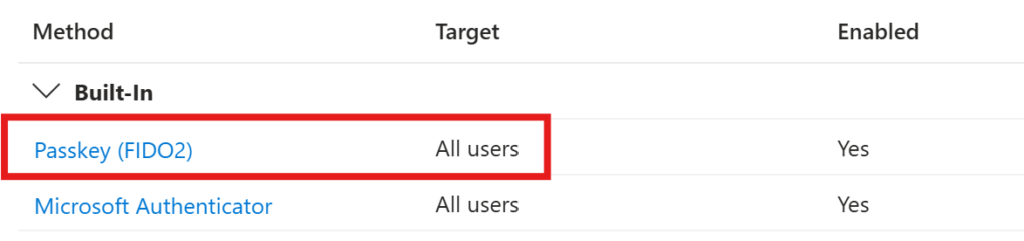
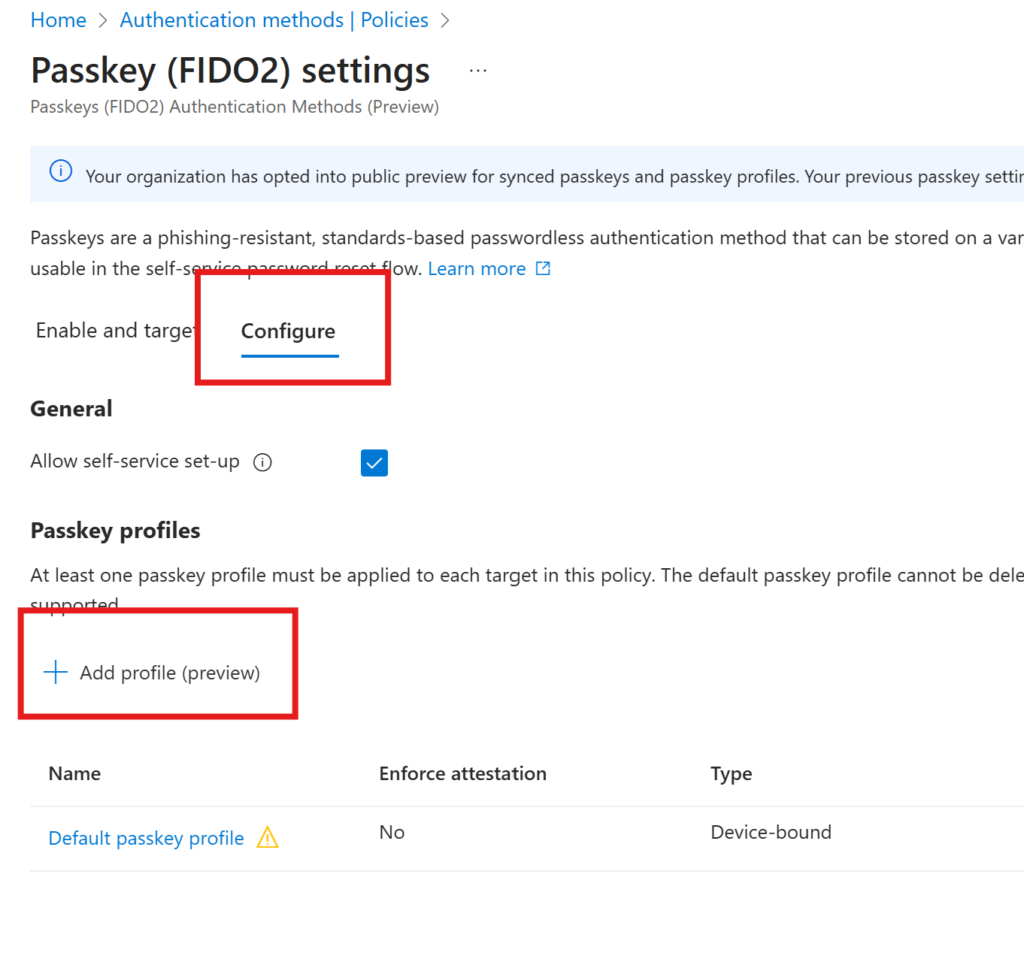
At the top, we need to Opt-In to the public preview settings. Currently it’s not possible to use passkeys in the password reset flow (SSPR) as an authentication method.
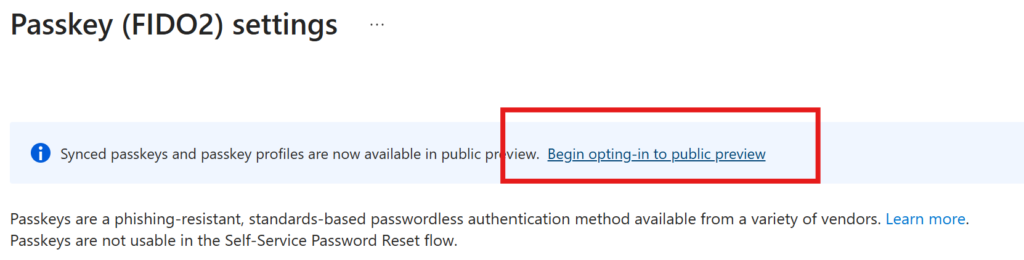
Since the configuration is changing (and we can have now up to 3 passkey profiles), we need to edit the default passkey profile before we can go on.
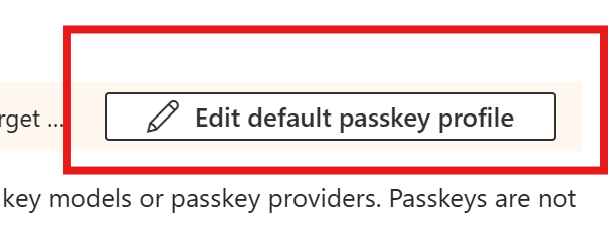
We now need to add the synced passkeys to the profile
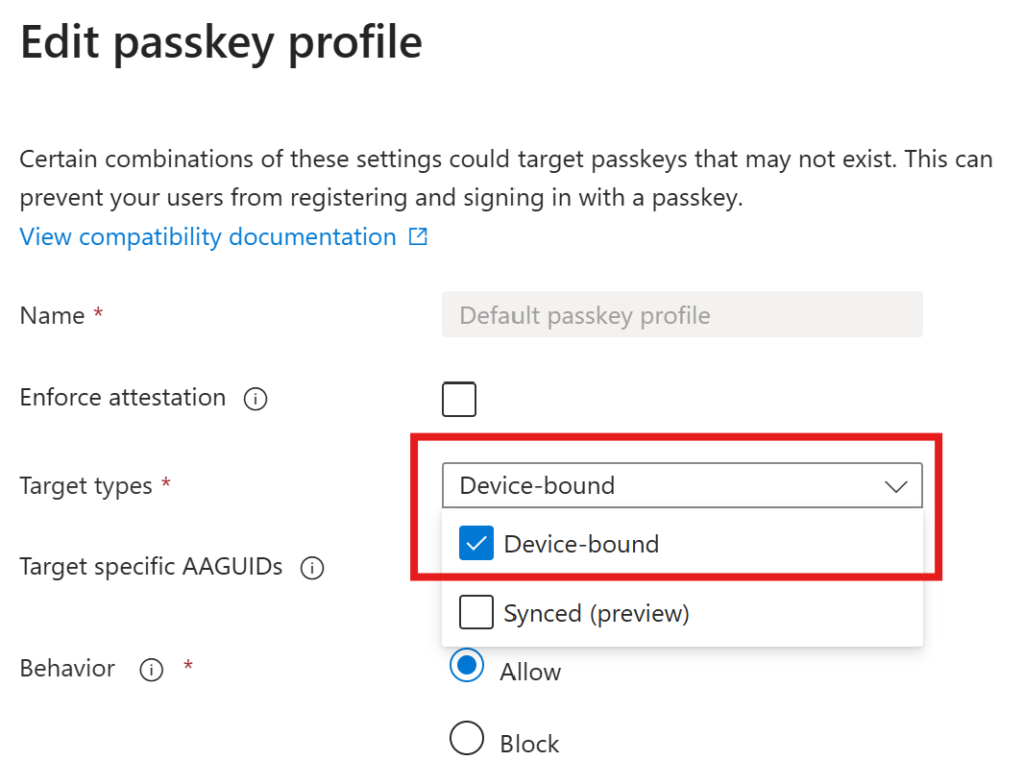
Attention: If you include the synced target type into the default profile, you cannot enforce attestation anymore! So for the default profile, we should just add device-bound and enable attestation. For users (test-users 😉) who should be able to use synced passkeys, we should create a separate profile and assign it accordingly!
To create the separate profile, go to the FIDO2 authentication method and create a new profile
Give it a telling name and set the target to synced. Also add the AAGUID of the passwordmanager of your choice, to control in what passwordmanagers the users will be able to save the passkeys.
If you are using AAGUID targeting, make sure you set the right behavior. It’s set to block by default and drove me crazy creating this guide. Well, at least I can say, the block feature works 😂
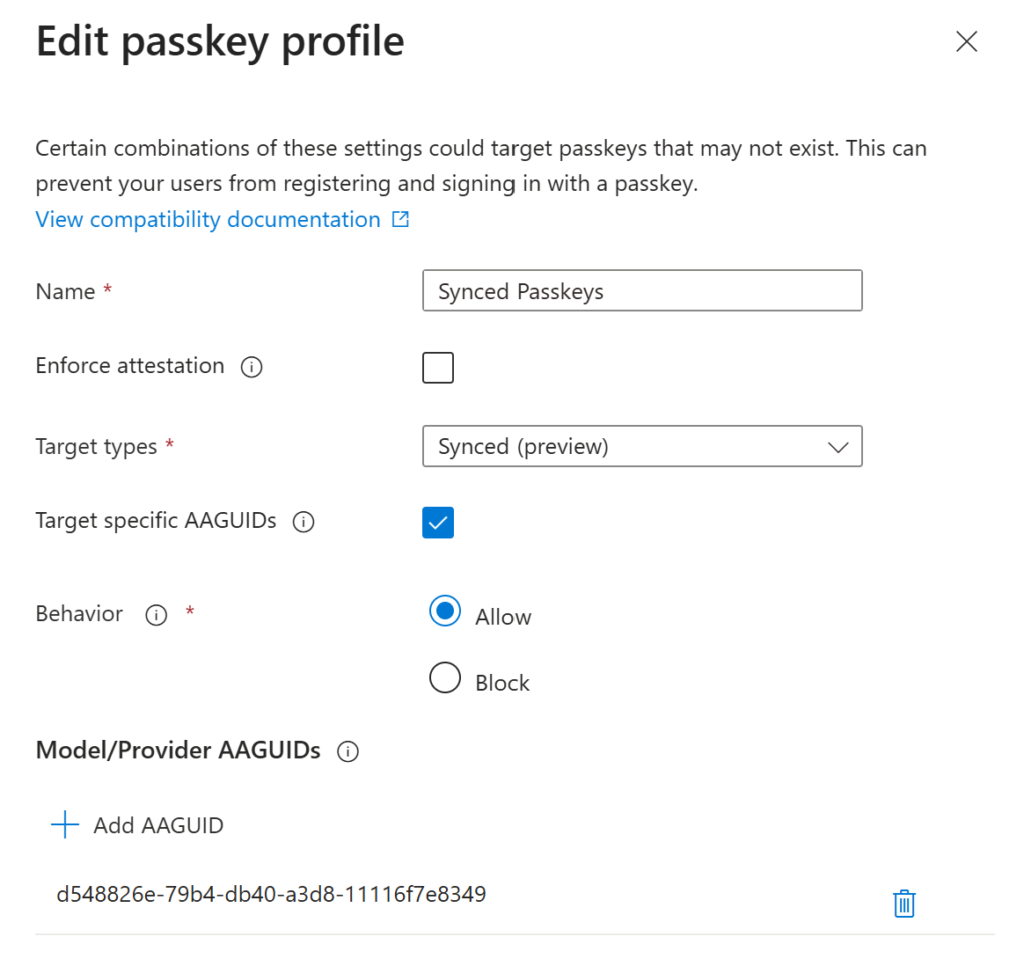
The AAGUID for Bitwarden is
d548826e-79b4-db40-a3d8-11116f7e8349
If you need to obtain other AAGUIDs use this list:
Passkeys Authenticator AAGUID Explorer
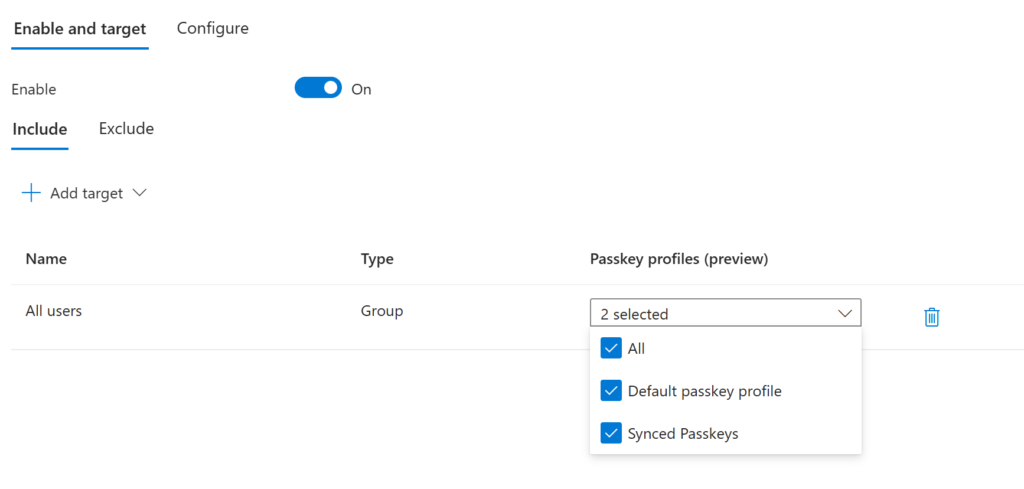
Go back to the passkey settings and assign the passkey profile accordingly
Setup passkey as MFA
Now active and unlock the Bitwarden (or any other passwordmanager) browser extension and go to https://aka.ms/mfasetup
Click on setup authentication method and choose “Passkey”
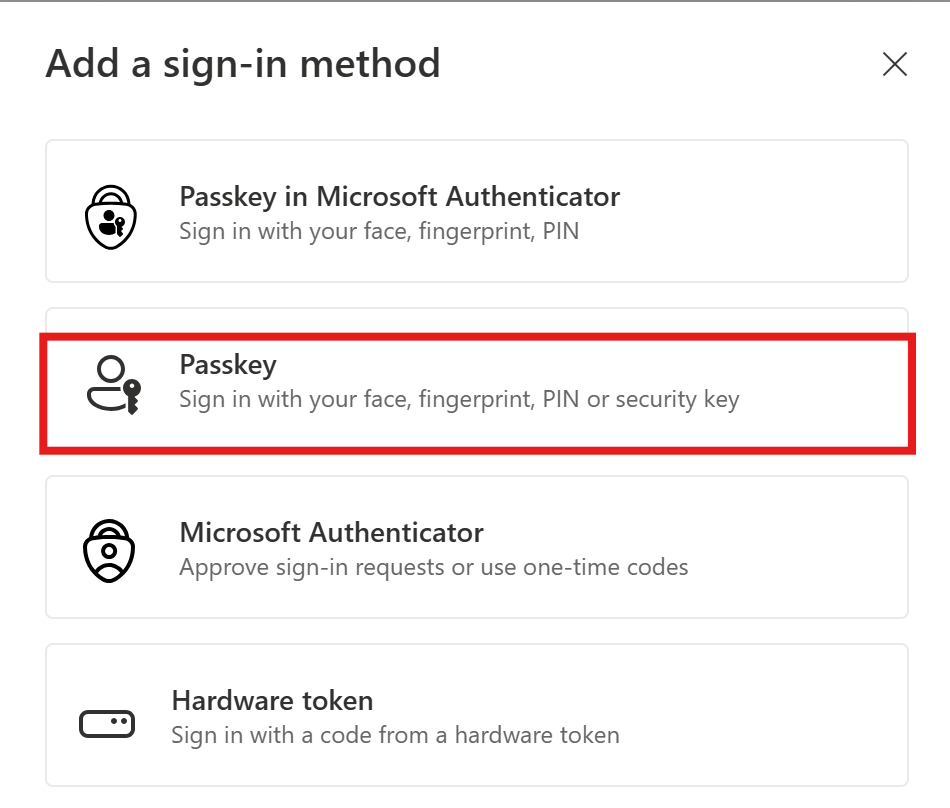
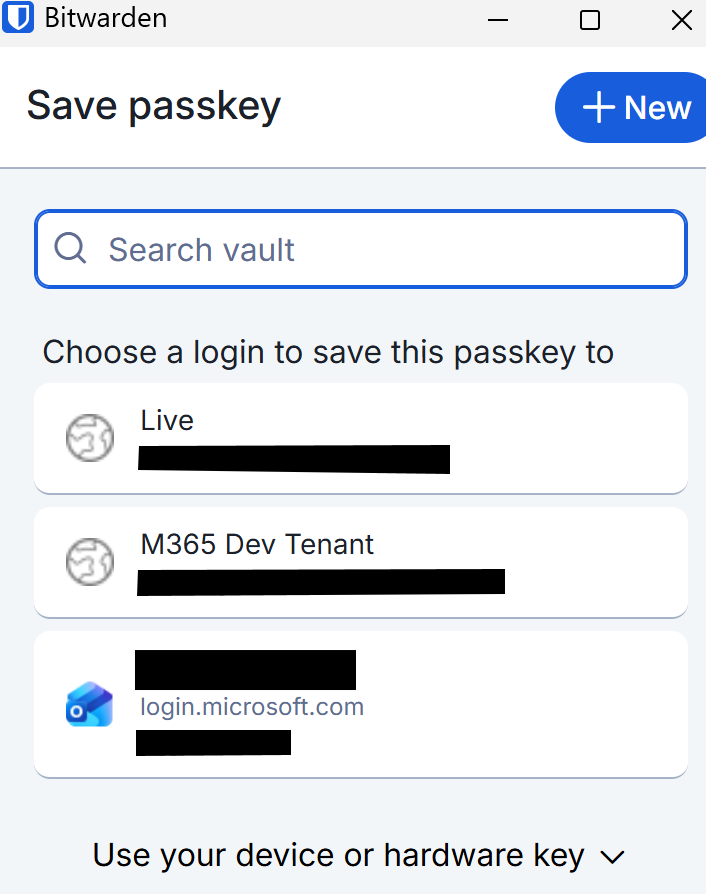
The browser extension should open and you can choose your saved credentials or create new ones (these are the credentials where the passkey will be saved)
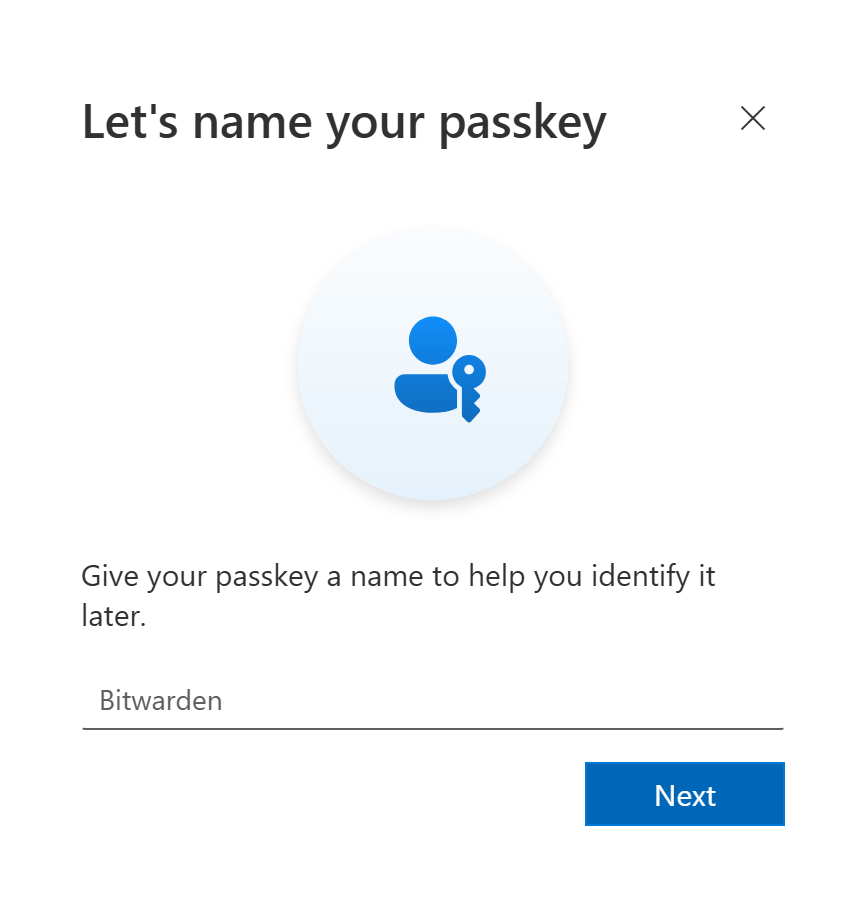
After choosing the credentials, you can name your authentication method accordingly
Done!!! You should now be able to see it as an authentication method

Now you should be able to login with a (synced) passkey.